Okta Setup Instructions & FAQ (SSO/SAML)
Set up one-click Knoetic access through Okta!
Your IT team will be required to assist with this configuration.
The following article will outline:
- How to configure your Okta & Knoetic SAML connection
- How to create an End-User Dashboard tile using Bookmark App Integration
Step-by-Step Instructions
- Contact your Okta Admin to create a new custom Okta application
- Use the following URL for the Single Sign-On URL
- https://login.knoetic.com/login/callback?connection=<your company name>-okta
For example: https://login.knoetic.com/login/callback?connection=demo-okta
- https://login.knoetic.com/login/callback?connection=<your company name>-okta
- Use the following URL for the Audience URI
- urn:auth0:knoetic:<your company name>-okta
For example: urn:auth0:knoetic:demo-okta
- urn:auth0:knoetic:<your company name>-okta
- Leave remaining fields blank/default
- Under the Attribute Statements section, add the following mappings:
- Name: given_name -> Value: user.firstName
- Name: family_name -> Value: user.lastName
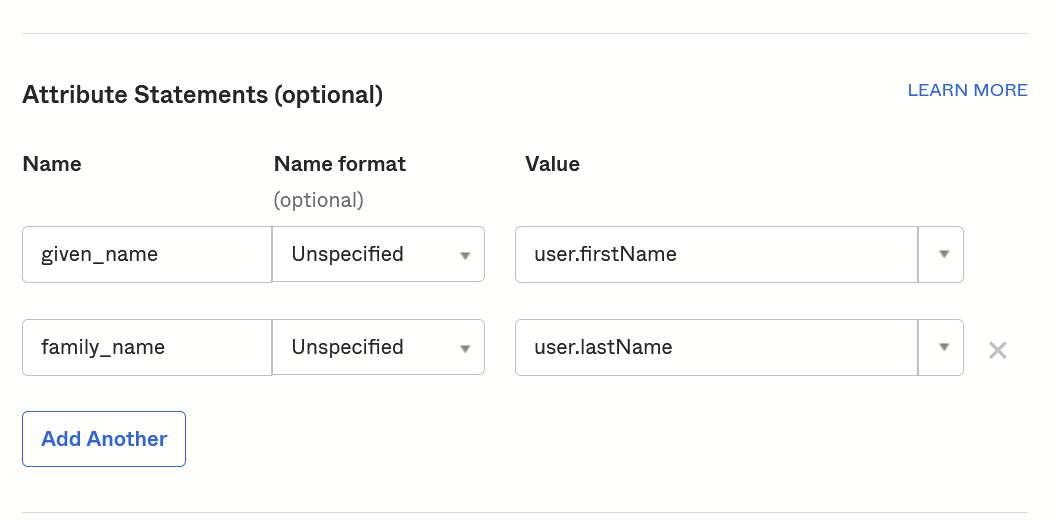
- Leave remaining sections blank/default and move to next step
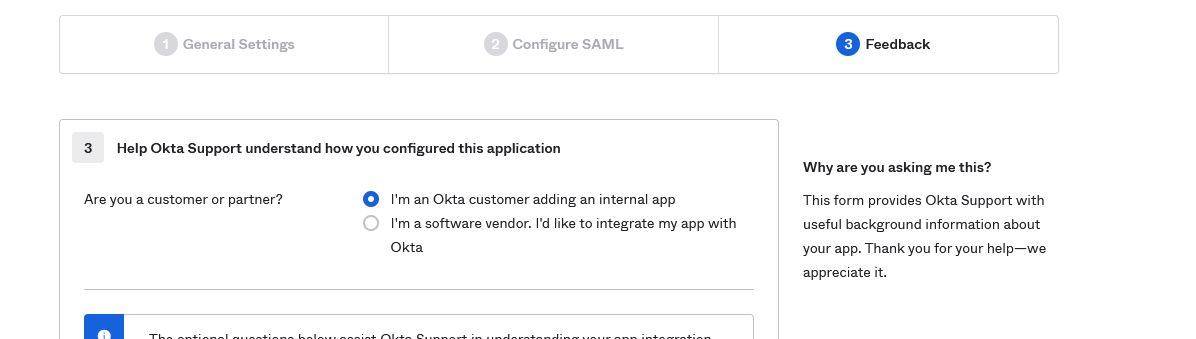
- On Section 3 "Feedback", select I'm an Okta customer adding an internal app
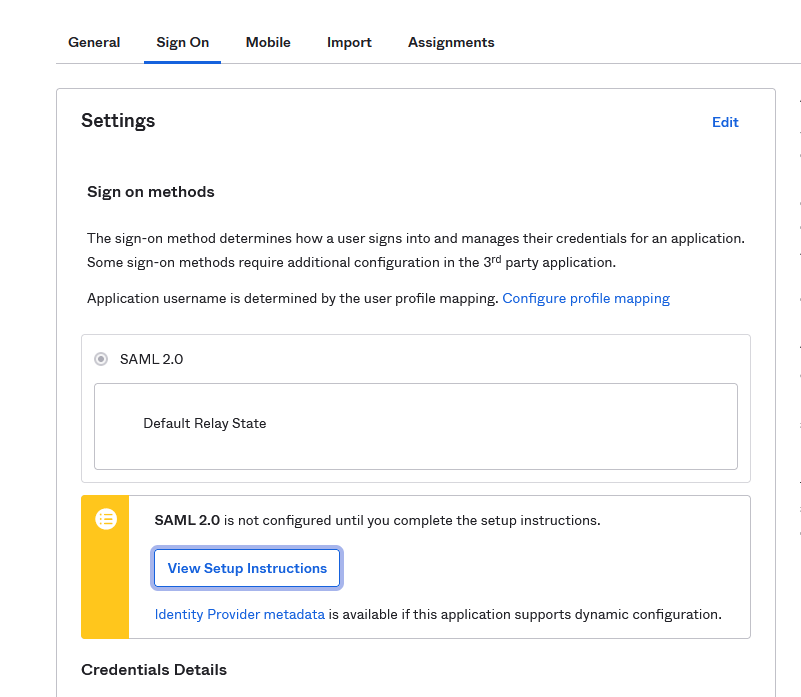
- Once the app is created, select View Setup Instructions
- Submit the follow through this Dropbox link:
- Download and attach X.509 Certificate
- Provide Identity Provider Single Sign-On URL in a document titled with the name of your Company.
- Our team will begin working on getting that set up and be in touch to test accounts, as needed, before issuing new user credentials.
- Note: Currently, we do not support IdP-initiated logins, so the newly created Okta Tile won't work when used. Users can instead log in from our Login page by choosing to Login with Okta. A workaround is to create a Knoetic Okta Bookmark Tile. See more in the next section.
Creating a Knoetic Okta Bookmark Tile
We do not currently support IdP-initiated logins, so the default Okta tile that gets created when you add the SAML application will result in an error when used.
Here is a suggested alternative:
- Get your company's custom login URL from your Customer Success representative (it will be in the form: https://app.knoetic.com/login?organization=<org_id>&connection=<connection_id>)
- Hide the application from the End-User Dashboard. DO NOT remove it, as it will break the SAML integration.
- Create a Bookmark App Integration that redirects to the Knoetic login URL you were provided
Questions?
Email success@knoetic.com to reach out Customer Success & Security team.
Additional Okta FAQs
Does Knoetic support JIT or SCIM provisioning via SAML, or do users need to be created within the application itself?
Knoetic does not currently support JIT provisioning of users in our system.
Is there a failover URL to login directly to Knoetic in case of issues with SAML?
Users can be set up with or without a password that they can use to login without SAML, so it's up to the client, on a per-user basis. For users with a password, they can login with that password regardless of whether SAML functionality is working from either Knoetic or the client's end.
What do we need to get started?
Just the answers to a few questions!
- Does your SAML integration send the employee email address as the user ID?

